
Authenticate with OpenID Connect
LogScale supports authenticating with any provider following the OpenID Connect standard. When OpenID Connect (OIDC) is configured, LogScale accepts OpenID tokens issued by the OpenID Connect provider (LogScale acts as a resource in OpenID Connect terms). This is useful if you are running LogScale behind a proxy that handles authentication.
In addition to acting as a resource, LogScale can also act as a client responsible for authenticating users (a relying party in OpenID Connect terms). This is similar to other OAuth authentication flows LogScale supports.
The diagram illustrates how OpenID Connect (OIDC) authentication works with LogScale. LogScale can function in two roles within the OIDC framework:
As a Resource where LogScale accepts tokens issued by an OIDC provider
As a Relying Party (Client) where LogScale handles authentication through an OIDC provider
Create an OpenID Connect app
Important
Prior to performing the steps below, make sure that you have a fully activated Okta account.
Log in and navigate to the main page of the Okta interface:
Click Adminto navigate to the Admin Dashboard. From there, click and select Applications.
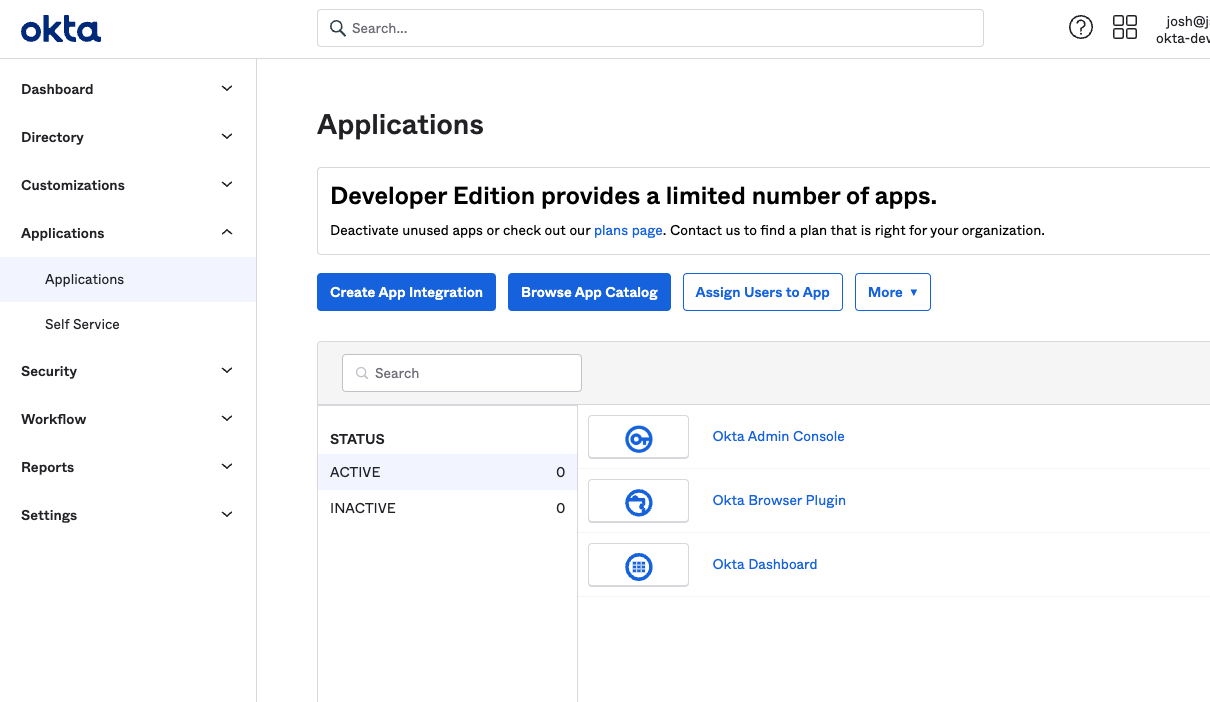
Figure 85. Navigating to the Applications Section in Okta
Next, click .
Figure 86. Starting the App Integration Process
Select and . Click .
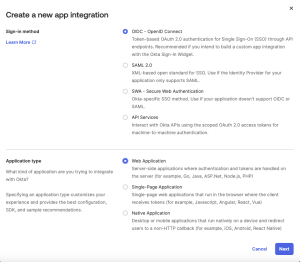
Figure 87. Selecting OpenID Connect App Type in Okta
Name the app, for example LogScale OIDC, and upload an image (optional). Enter the following:
Grant Type: Client Credentials
Sign-in redirect URLs: $LOGSCALE_URL/auth/oidc
Sign-out redirect URLs: remove, if existing. Optional.
Assignments: Select Skip Group Assignment for now
Click .
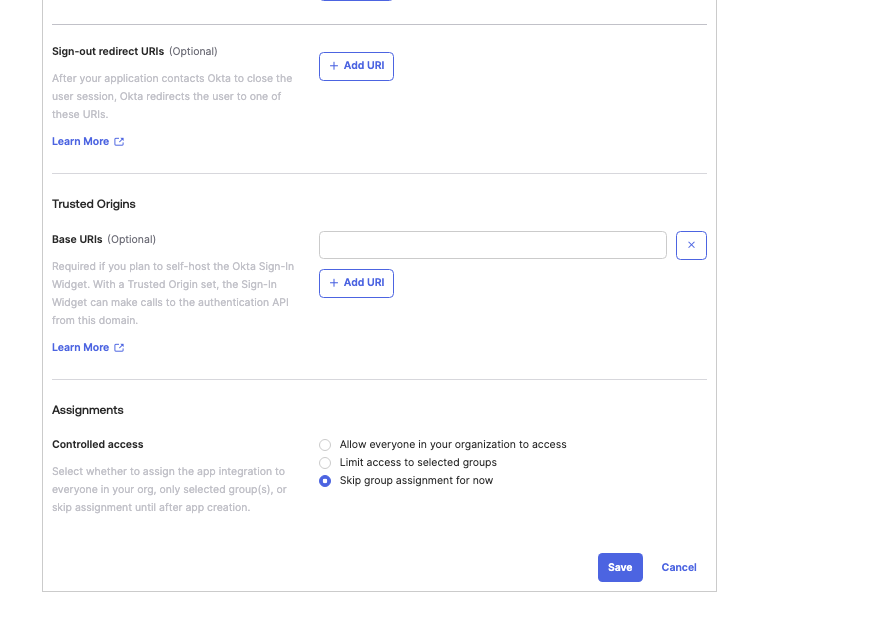
Figure 88. Configuring OIDC Application Settings in Okta
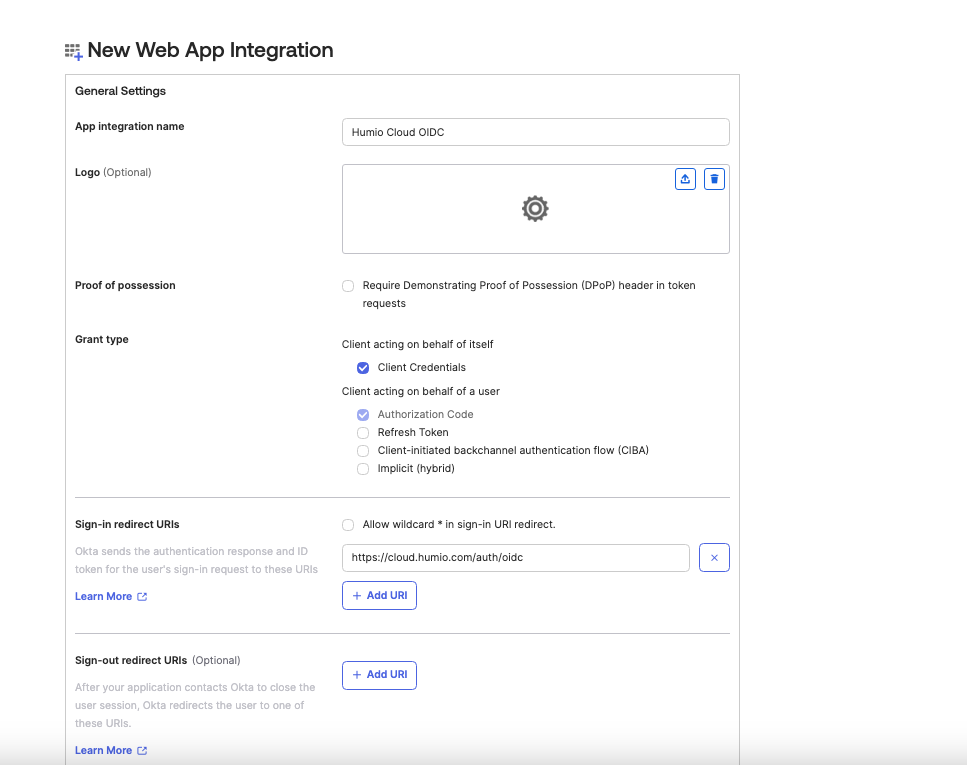
Figure 89. Configuring Redirect URLs and Assignments in Okta
Click the Sign On tab of the app, and under OpenID Connect ID Token Set Issuer to Okta URL (https://dev-84903084.okta.com). Set Group claims filter to
groupsand selectMatches regexwith the regex pattern.*. Click .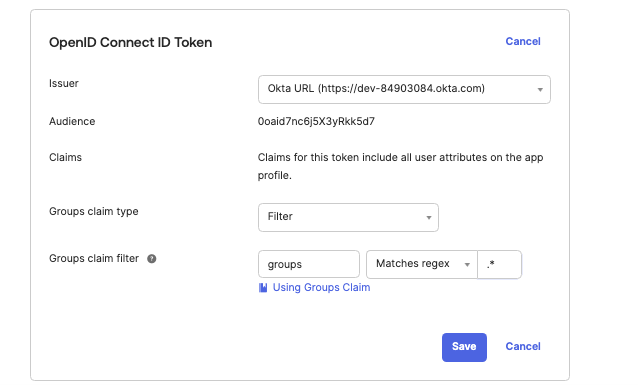
Figure 90. Configuring Group Claims in OpenID Connect ID Token
Configure LogScale to use OpenID Connect
To configure OpenID Connect to work with LogScale_, contact Support.