
zscaler/internet-access
| Vendor | Zscaler, Inc. | Parsers | ✓ |
| Author | CrowdStrike | Dashboards | ✓ |
| Version | 2.1.0 | Alerts | ✗ |
| Minimum LogScale Version | 1.207.0 | Actions | ✗ |
| Use Cases | ITOps SecOps | Scheduled Searches | ✗ |
| Supported Log Formats |
| ||
| Security Domain | Cloud & Web Security |
| Field | Format | Timezone |
|---|---|---|
| Vendor.datetime | yyyy-MM-dd HH:mm:ss | UTC |
| Vendor.datetime | EEE MMM [ ]d HH:mm:ss yyyy | UTC |
| Vendor.lastmodtime | E MMM [ ]d HH:mm:ss yyyy | UTC |
| Vendor.time | EEE MMM [ ]d HH:mm:ss yyyy | UTC |
Monitor Zscaler™ for suspicious activity more efficiently by correlating Zscaler™ events with other sources in LogScale.
Quickly find early indicators of attack or insider threats by looking at proxy traffic summaries per user, file downloads directly from an IP address and more.
Breaking Changes
This update includes parser changes, which means that data ingested after upgrade will not be backwards compatible with logs ingested with the previous version.
Updating to version 1.0.0 or newer will therefore result in issues with existing queries in for example dashboards or alerts created prior to this version.
See CrowdStrike Parsing Standard (CPS) 1.0 for more details on the new parser schema.
Installing the Package in LogScale
Find the repository where you want to send the Zscaler events, or Creating a Repository or View.
Navigate to your repository in the LogScale interface, click Settings and then on the left.
Click and install the LogScale package for Zscaler (i.e. zscaler/zia).
When the package has finished installing, click on the left (still under the , see Figure 55, “Ingest Token”).
In the right panel, click to create a new token. Give the token an appropriate name (the name of the event hub it will collect logs from), and assign the parser that was installed with the package zscaler.
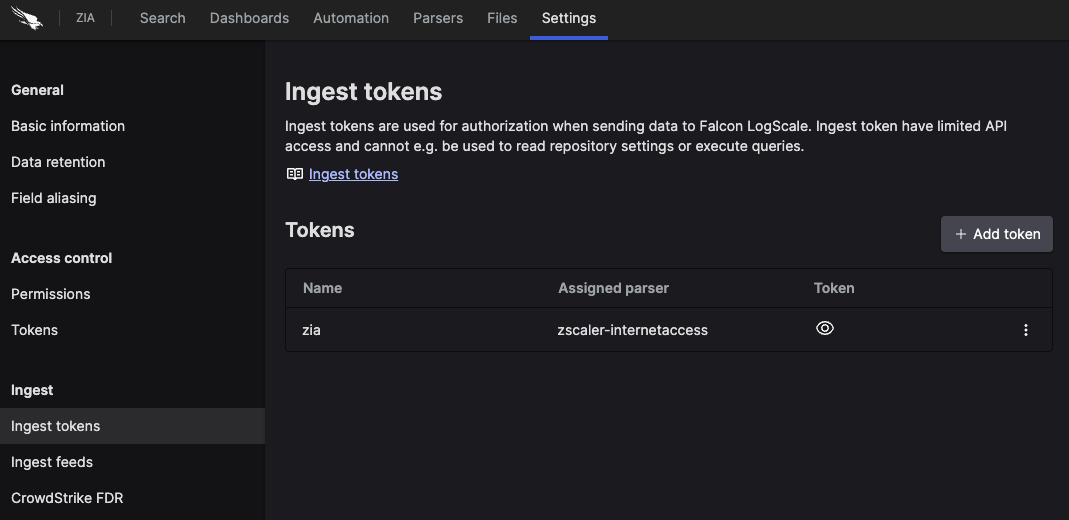
Figure 55. Ingest Token
Before leaving this page, view the ingest token and copy it to your clipboard — to save it temporarily elsewhere.
Now that you have a repository set up in LogScale along with an ingest token you're ready to send logs to LogScale.
Configurations and Sending the Logs to LogScale
To get logs from Zscaler ZIA into LogScale, you can use Zscaler Nanolog Streaming Service (NSS), which comes in two variants:
Cloud NSS, which allows you to send logs directly to LogScale
VM-based NSS, which allows you to collect logs on a VM, where they can be sent to LogScale via syslog
Cloud NSS
Configure the NSS feeds as follows:
Set as "Other"
Set the API URL as the URL for your LogScale cluster with the text
/api/v1/ingest/hec/rawappended, to point to the ingest API.Add a HTTP header, so that
Key1has the text Authorization andValue1has the value:Bearer TOKENWhere the token is the ingest token for your given feed.
Important
The HTTP header value must include the word
Bearerfollowed by the token.If you are making a Web feed, then use the token that you assigned the zscalernss-web parser to in the previous step, and likewise for the other types.
Select as the Feed Output Type, and copy the given format for your feed type from the sections below.
In the list, enter these characters: ",\ (that is: double quote, comma, backslash)
VM-Based NSS
For VM-based NSS, you need the following:
NSS servers up and running.
A Falcon LogScale Collector that is accessible from the NSS server, and configured to receive syslog events over TCP, and forwarding them to LogScale. You can find an example syslog configuration in Configuration Examples for the log collector handling syslog in the library.
For the feed configuration inside NSS, or SIEM Destination Type, select .
For SIEM IP Address and SIEM TCP Port, insert the IP address and port where your log collector is listening for data.
For the Feed Output Type, select and copy the given format for your feed type from the sections below.
In the Feed Escape Character list, enter these characters: ",\ (that is: double quote, comma, backslash)
Note
You can add any fields you would like to these formats, and they will be present and usable in LogScale, but they will only be mapped to the schema if you manually extend the parsers to handle those fields.
DNS
DNS configuration:
\{ "sourcetype" : "zscalernss-dns", "event" :\{"datetime":"%d{yy}-%02d{mth}-%02d{dd} %02d{hh}:%02d{mm}:%02d{ss}","user":"%s{elogin}","department":"%s{edepartment}","location":"%s{elocation}","reqaction":"%s{reqaction}","resaction":"%s{resaction}","reqrulelabel":"%s{reqrulelabel}","resrulelabel":"%s{resrulelabel}","dns_reqtype":"%s{reqtype}","dns_req":"%s{req}","dns_resp":"%s{res}","srv_dport":"%d{sport}","durationms":"%d{durationms}","clt_sip":"%s{cip}","srv_dip":"%s{sip}","category":"%s{domcat}","respipcategory":"%s{respipcat}","deviceowner":"%s{deviceowner}","devicehostname":"%s{devicehostname}"\}\}Firewall
Firewall configuration:
\{ "sourcetype" : "zscalernss-fw", "event" :\{"datetime":"%d{yy}-%02d{mth}-%02d{dd} %02d{hh}:%02d{mm}:%02d{ss}","user":"%s{elogin}","department":"%s{edepartment}","locationname":"%s{elocation}","cdport":"%d{cdport}","csport":"%d{csport}","sdport":"%d{sdport}","ssport":"%d{ssport}","csip":"%s{csip}","cdip":"%s{cdip}","ssip":"%s{ssip}","sdip":"%s{sdip}","tsip":"%s{tsip}","tunsport":"%d{tsport}","tuntype":"%s{ttype}","action":"%s{action}","dnat":"%s{dnat}","stateful":"%s{stateful}","aggregate":"%s{aggregate}","nwsvc":"%s{nwsvc}","nwapp":"%s{nwapp}","proto":"%s{ipproto}","ipcat":"%s{ipcat}","destcountry":"%s{destcountry}","avgduration":"%d{avgduration}","rulelabel":"%s{erulelabel}","inbytes":"%ld{inbytes}","outbytes":"%ld{outbytes}","duration":"%d{duration}","durationms":"%d{durationms}","numsessions":"%d{numsessions}","ipsrulelabel":"%s{ipsrulelabel}","threatcat":"%s{threatcat}","threatname":"%s{ethreatname}","deviceowner":"%s{deviceowner}","devicehostname":"%s{devicehostname}"\}\}Web
Web configuration:
\{ "sourcetype" : "zscalernss-web", "event" : \{"datetime":"%d{yy}-%02d{mth}-%02d{dd} %02d{hh}:%02d{mm}:%02d{ss}","reason":"%s{reason}","event_id":"%d{recordid}","protocol":"%s{proto}","action":"%s{action}","transactionsize":"%d{totalsize}","responsesize":"%d{respsize}","requestsize":"%d{reqsize}","urlcategory":"%s{urlcat}","serverip":"%s{sip}","clienttranstime":"%d{ctime}","requestmethod":"%s{reqmethod}","refererURL":"%s{b64referer}","useragent":"%s{eua}","product":"NSS","location":"%s{elocation}","ClientIP":"%s{cip}","status":"%s{respcode}","user":"%s{elogin}","url":"%s{b64url}","vendor":"Zscaler","hostname":"%s{ehost}","clientpublicIP":"%s{cintip}","threatcategory":"%s{malwarecat}","threatname":"%s{threatname}","filetype":"%s{filetype}","appname":"%s{appname}","pagerisk":"%d{riskscore}","department":"%s{edepartment}","urlsupercategory":"%s{urlsupercat}","appclass":"%s{appclass}","dlpengine":"%s{dlpeng}","urlclass":"%s{urlclass}","threatclass":"%s{malwareclass}","dlpdictionaries":"%s{dlpdict}","fileclass":"%s{fileclass}","bwthrottle":"%s{bwthrottle}","servertranstime":"%d{stime}","contenttype":"%s{contenttype}","unscannabletype":"%s{unscannabletype}","deviceowner":"%s{deviceowner}","devicehostname":"%s{devicehostname}", "decrypted": "%s{ssldecrypted}"\}\}Tunnel
Tunnel events have multiple possible event types, which each have their own formats. Configure them as follows:
Tunnel Events :
\{ "sourcetype" : "zscalernss-tunnel", "event" : \{"datetime":"%s{datetime}","Recordtype":"%s{tunnelactionname}","tunneltype":"%s{tunneltype}","user":"%s{vpncredentialname}","location":"%s{elocationname}","sourceip":"%s{sourceip}","destinationip":"%s{destvip}","sourceport":"%d{srcport}","event":"%s{event}","eventreason":"%s{eventreason}","recordid":"%d{recordid}"\}\}Tunnel Samples :
\{ "sourcetype" : "zscalernss-tunnel", "event" : \{"datetime":"%s{datetime}","Recordtype":"%s{tunnelactionname}","tunneltype":"%s{tunneltype}","user":"%s{vpncredentialname}","location":"%s{elocationname}","sourceip":"%s{sourceip}","destinationip":"%s{destvip}","sourceport":"%d{srcport}","txbytes":"%lu{txbytes}","rxbytes":"%lu{rxbytes}","dpdrec":"%d{dpdrec}","recordid":"%d{recordid}"\}\}IKE phase 1 :
\{ "sourcetype" : "zscalernss-tunnel", "event" : \{"datetime":"%s{datetime}","Recordtype":"%s{tunnelactionname}","tunneltype":"IPSEC IKEV %d{ikeversion}","user":"%s{vpncredentialname}","location":"%s{elocationname}","sourceip":"%s{sourceip}","destinationip":"%s{destvip}","sourceport":"%d{srcport}","destinationport":"%d{dstport}","lifetime":"%d{lifetime}","ikeversion":"%d{ikeversion}","spi_in":"%lu{spi_in}","spi_out":"%lu{spi_out}","algo":"%s{algo}","authentication":"%s{authentication}","authtype":"%s{authtype}","recordid":"%d{recordid}"\}\}IKE phase 2 :
\{ "sourcetype" : "zscalernss-tunnel", "event" : \{"datetime":"%s{datetime}","Recordtype":"%s{tunnelactionname}","tunneltype":"IPSEC IKEV %d{ikeversion}","user":"%s{vpncredentialname}","location":"%s{elocationname}","sourceip":"%s{sourceip}","destinationip":"%s{destvip}","sourceport":"%d{srcport}","sourceportstart":"%d{srcportstart}","destinationportstart":"%d{destportstart}","srcipstart":"%s{srcipstart}","srcipend":"%s{srcipend}","destinationipstart":"%s{destipstart}","destinationipend":"%s{destipend}","lifetime":"%d{lifetime}","ikeversion":"%d{ikeversion}","lifebytes":"%d{lifebytes}","spi":"%d{spi}","algo":"%s{algo}","authentication":"%s{authentication}","authtype":"%s{authtype}","protocol":"%s{protocol}","tunnelprotocol":"%s{tunnelprotocol}","policydirection":"%s{policydirection}","recordid":"%d{recordid}"\}\}EDLP :
\{ "sourcetype" : "zscalernss-edlp", "event" :\{"datetime":"%d{yy}-%02d{mth}-%02d{dd}-%02d{hh}:%02d{mm}:%02d{ss}-%s{tz}","recordid":"%d{recordid}","login":"%s{user}","dept":"%s{department}","filetypename":"%s{filetypename}","filemd5":"%s{filemd5}","dlpdictnames":"%s{dlpdictnames}","dlpdictcount":"%s{dlpcounts}","dlpenginenames":"%s{dlpengnames}","channel":"%s{channel}","actiontaken":"%s{actiontaken}","severity":"%s{severity}","rulename":"%s{triggeredrulelabel}","itemdstname":"%s{itemdstname}"\}\}Audit :
\{ "sourcetype" : "zscalernss-audit", "event" :\{"time":"%s{time}","recordid":"%d{recordid}","action":"%s{action}","category":"%s{category}","subcategory":"%s{subcategory}","resource":"%s{resource}","interface":"%s{interface}","adminid":"%s{adminid}","clientip":"%s{clientip}","result":"%s{result}","errorcode":"%s{errorcode}","auditlogtype":"%s{auditlogtype}","preaction":%s{preaction},"postaction":%s{postaction}\}\}Casb :
\{ "sourcetype" : "zscalernss-casb", "event" :\{"datetime":"%d{yy} %02d{mth} %02d{dd} %02d{hh} %02d{mm} %02d{ss}","recordid":"%d{recordid}","company":"%s{company}","tenant":"%s{tenant}","login":"%s{user}","dept":"%s{department}","applicationname":"%s{applicationname}","filename":"%s{filename}","filesource":"%s{filesource}","filemd5":"%s{filemd5}","threatname":"%s{threatname}","policy":"%s{policy}","dlpdictnames":"%s{dlpdictnames}","dlpdictcount":"%s{dlpdictcount}","dlpenginenames":"%s{dlpenginenames}","fullurl":"%s{fullurl}","lastmodtime":"%s{lastmodtime}","filescantimems":"%d{filescantimems}","filedownloadtimems":"%d{filedownloadtimems}"\}\}Verify Data is Arriving in LogScale
Once you have completed the above steps the ZIA logs should be arriving in your LogScale repository.
You can verify this by doing a simple search for
#Vendor = "zscaler" | #event.module = "zia" to see
the events.