
vectra/detections
| Vendor | Vectra AI, Inc. | Parsers | ✓ |
| Author | vectra | Dashboards | ✓ |
| Version | 0.1.0 | Alerts | ✗ |
| Minimum LogScale Version | 1.20.0 | Actions | ✗ |
| Scheduled Searches | ✗ |
Vectra AI protects businesses by detecting and stopping cyberattacks. As a leader in network detection and response (NDR), Vectra AI protects your data, systems, and infrastructure. Vectra AI enables your SOC team to quickly discover and respond to attackers before they act.
Vectra AI rapidly identifies suspicious behavior and activity on your extended network, whether on-premises or in the cloud. Vectra will find it, flag it, and alert security personnel so they can respond immediately. Vectra AI is Security that thinks.
Vectra AI uses artificial intelligence to improve detection and response over time, eliminating false positives so you can focus on real threats.
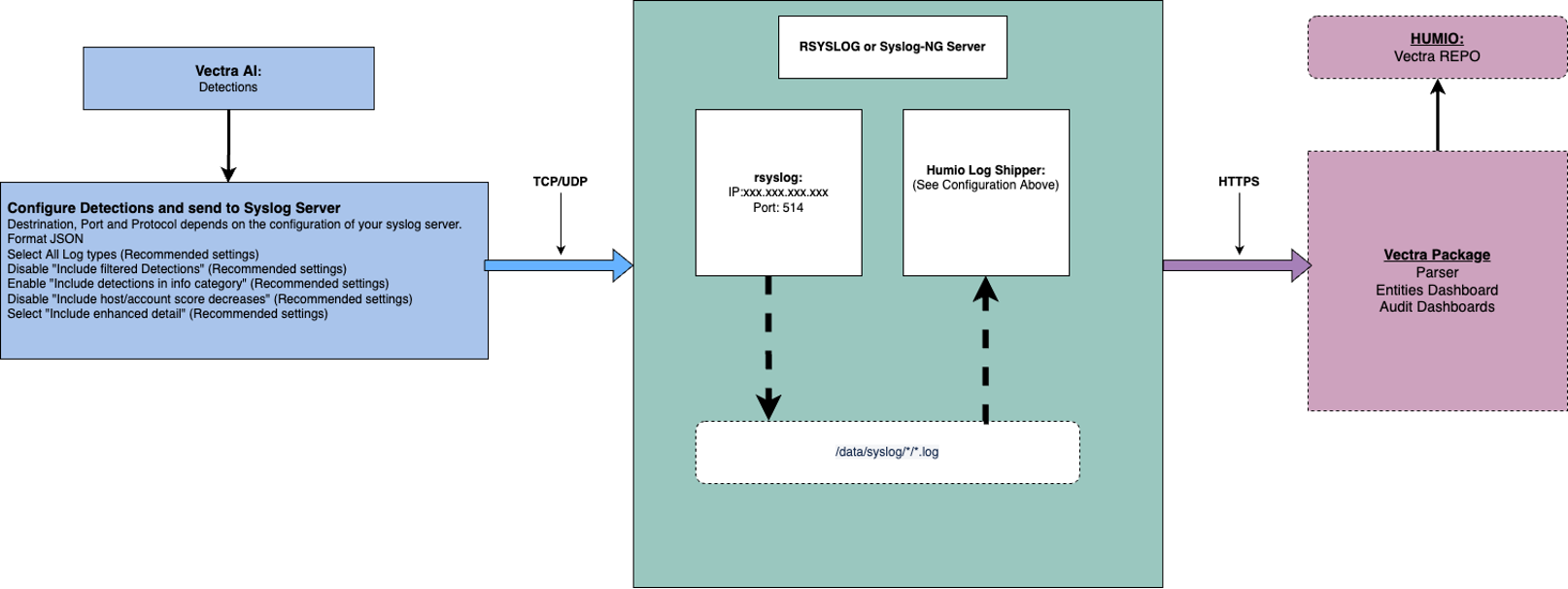 |
Figure 54. Vectra AI Integration
For more details about Vectra and how we use AI to detect attacker behavior, please visit our website
Configure Ingestion to LogScale
Install this package in the relevant repository and create a new ingest token for the Vectra Detect parser and copy this token value. Assign the parser from this package to the token.
(Optional) if not already in place, send the Vectra AI Detect events (in JSON) to a Syslog server (e.g Syslog-ng or rsyslog). From Vectra Detect UI, navigate to Settings → Notification → Syslog and configure a new destination to the syslog server:
Destination, Port and Protocol depends on the configuration of your syslog server.
Format JSON
Select All Log types (Recommended settings)
Disable Include filtered Detections (Recommended settings)
Enable Include detections in info category (Recommended settings)
Disable Include host/account score decreases (Recommended settings)
Select Include enhanced detail (Recommended settings)
Setup the Falcon LogScale Collector. Sample configuration file (
/etc/humio-log-collector/config.yaml):dataDirectory: /var/lib/humio-log-collector sources: vectra_detect: type: file include: /data/syslog/*/*.log exclude: /data/syslog/*/*.gz sink: community_humio sinks: community_humio: type: humio token: xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx url: https://HUMIO_URL
Install the Falcon LogScale Collector package then
edit the configuration file
(config.yaml) as you
see above. Once configured you can look at the dashboards or,
alternatively, go to your LogScale search window and type
#type=Vectra-Detect
Preparations in LogScale
You will need to create a new repository for your Vectra data. If you aren't sure how to do this, see Creating a Repository or View.
Once you've created a new repository, click on the Settings tab and then Packages along the left-hand column. From there, chose Marketplace and search for, then install the LogScale package for Vectra AI.
Upon selecting the Vectra package, it will describe what the package provides and other related information. Of most interest is that it will install the required Vectra-Detect parser. Also included will be two dashboards and an action.
After installing the Vectra Package, you will need to create an Ingest Token under the Ingest heading on the left panel. You will click you will name it and assign the Vectra-Detect parser that was installed with the package
After clicking you will be presented with a dialog box showing the new ingest token. You will click the "eye" token and be presented with the ingest token for your Vectra data.
You then click icon and this value is pasted into
dest_token = e7afd72e-560f-4599-bdbe-b61e31e1426b #-From Step 3 in "Configure Ingestion to LogScale"You should now be seeing Vectra Detections arriving in your LogScale repository and the dashboards should begin populating.