
mimecast/email-security
| Vendor | Mimecast Services Ltd. | Parsers | ✓ |
| Author | Mimecast | Dashboards | ✓ |
| Version | 1.0.0 | Alerts | ✗ |
| Minimum LogScale Version | 1.145.0 | Actions | ✗ |
| Supported Log Formats |
| Scheduled Searches | ✗ |
Mimecast delivers a comprehensive, integrated solution that protects the premier cybersecurity attack vector. Learn more at Mimecast.
The Mimecast email security product is a SaaS based service that includes multi-layered protection and targeted threat protection. Capabilities include anti-virus, anti-spam, attachment and URL security, DLP, impersonation protection and threat intelligence.
Mimecast and LogScale provide an integrated solution to improve detection, stop threats and provide security insights gathered across the organization. With LogScale customers can ingest Mimecast logs along with other log sources to get complete visibility across their environments. Email security logs are a valuable source of data for cyber defence teams. LogScale customers can correlate Mimecast insights with logs from network, endpoint and other systems to search for IOCs and other signs of potentially malicious activity in order to reduce detection times and increase the speed and completeness of cyber investigations.
By integrating Mimecast and LogScale customers can gain the following benefits:
Add context to your Mimecast logs by correlating with other log sources including infrastructure, network and software logs.
Get more value from Mimecast IOC detections by searching for these across other log sources.
Empower threat hunters with blazing fast search across logs from the primary attack vector, email.
Enable investigations to uncover the full kill-chain right back to the initial compromise - which is often an email based attack vector
Contain attacks earlier with rapid detections and response to phishing and business email compromise tactics.
Configure Mimecast and LogScale integration
Mimecast have developed a middle-ware component that pulls the required logs from Mimecast and sends them into LogScale. Mimecast have also developed a free package in the LogScale marketplace which includes the parser and dashboards — one for each of the following types of Mimecast logs — Audit, Data Leak, Threat Intel Regional, Impersonation Protect, URL Protect, Attachment Protect, Email Activity Summary, Awareness Training and Threat Intel Targeted. If you wish to you can exclude certain log types in the configuration of the middle-ware component.
Enabling the integration involves installing the Mimecast package in LogScale, installing and configuring the Mimecast middle-ware that handles the log ingestion.
Create a new repository in LogScale for the Mimecast data. From the target repository select
Settings and Packagesand install the Mimecast Package from the LogScale marketplace.The package will install the mimecast-emailsecruity parser as well as some overview dashboards which you can edit later if required.
From the Mimecast repository select
Settingsand underIngestchooseAPI Tokensand create a new token and assign it themimecast-emailsecurityparser. Copy the token.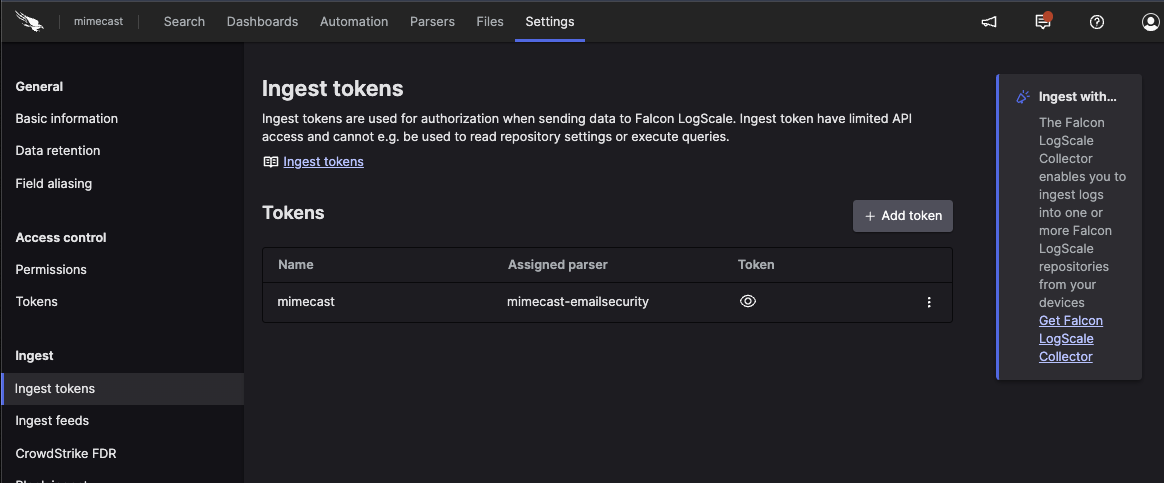
Figure 25. Configure Ingest Tokens
Now install and configure the Mimecast middle-ware component are provided here: here. The middle-ware component requires the following LogScale details:
base_url— The URL to your LogScale service.logscale_api_token— The API token you copied earlier from the LogScale interface.repo_name— The LogScale repository name you created in step (1) within your LogScale account.
You should now see Mimecast logs appearing in your LogScale repository and the dashboards start to populate with data. You can verify this by checking in the main LogScale menu that you can see the 9 dashboards configured and the volume of ingested logs (in the example below 3.6G bytes)
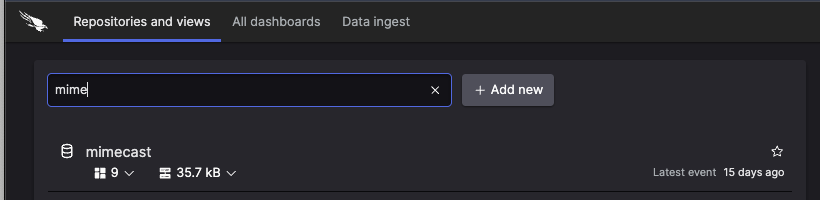
Figure 26. Mimecast Data in Repository