
ordr/ordr
| Vendor | Ordr, Inc. | Parsers | ✓ |
| Author | Ordr Inc | Dashboards | ✓ |
| Version | 0.1.0 | Alerts | ✗ |
| Minimum LogScale Version | 1.50.0 | Actions | ✗ |
| Scheduled Searches | ✗ |
Ordr makes it easy to secure every connected device, from traditional IT devices to newer and more vulnerable IoT, IoMT, and OT. Ordr Systems Control Engine uses deep packet inspection and advanced machine learning to discover every device, profile its risk and behavior, map all communications and protect it with automated policies.
Ordr collects managed device data and threat insights, includes vulnerabilities from CrowdStrike for comprehensive device visibility, a better understanding of risk, and the ability to enforce policy to mitigate active threats and improve security across all connected devices.
Integration with CrowdStrike Falcon LogScale enables organizations to run advance device and risk analyses by leveraging the correlated telemetry from CrowdStrike and Ordr. See https://ordr.net/ for more information.
Install the Package in LogScale
Find the repository where you want to send the logs, or create a new one.
Navigate to your repository in the LogScale UI, click Settings and then on the left.
Click and install the LogScale package for Ordr (i.e. ordr/ordr)
When the package has finished installing, click on the left (still under the ).
In the right panel, click to create a new token. Give the token an appropriate name (the name of the event hub it collect logs from), and assign the parser Ordr.
Before leaving this page, view the ingest token and copy it to your clipboard — to save it temporarily elsewhere.
Now that you have a repository set up in LogScale along with an ingest token you're ready to send logs to LogScale.
Configure Ingest to LogScale
Go to the Ordr UI:
Go to the Integrations tab, and click under External Services and Tools Integration table
In the Service Detail window, enter the newly created ingest token for as the LogScale Token and choose the LogScale Endpoint based on your LogScale Instance.
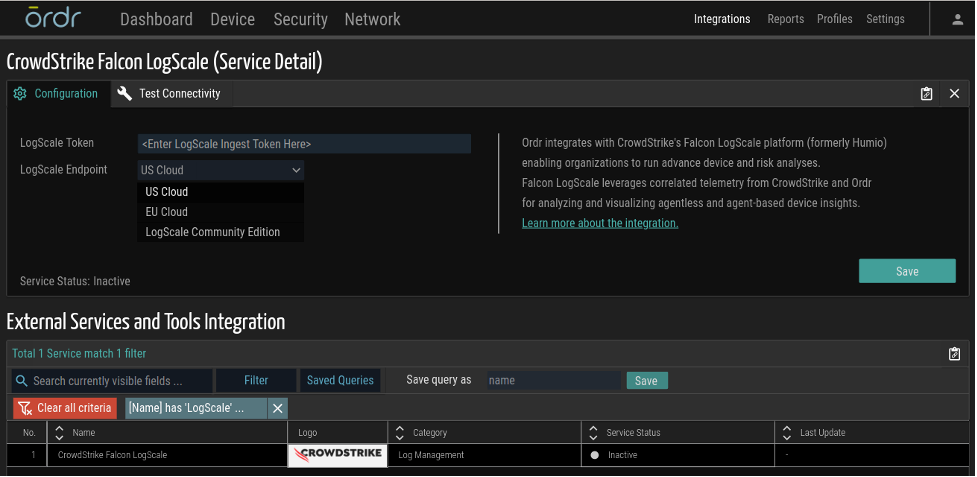
Figure 39. Ordr Configuration