
CrowdStrike FLTR Firewall Adversaries
CrowdStrike tracks and profiles hundreds of adversaries, and indicator of compromise (IOC) details stream into Falcon Long Term Repository hourly. Adversaries are motivated by specific objectives including financial/political gain, and espionage. This package provides a preview parser/s for Falcon FLTR Firewall data, and is designed to help you visualize which adversaries are targeting your firewalls.
Note that your firewall data must be normalized and an active FLTR license must be in place for this dashboard to work. Users must also add firewall parsers from LogScale marketplace to their ingest feeds to get started. This package was tested using data parsed by the LogScale Marketplace Palo Alto Firewall parser, see Palo Alto Network Firewall Logs.
Configurations and Sending The Logs to LogScale
Data for users who have Falcon Long Term Repository licenses will be available automatically. For setting up ingest and parsing of firewall data, refer to the Palo Alto specification manual.
Installing the FLTR Firewall Adversaries Dashboard
CrowdStrike FLTR Firewall Adversaries Dashboard is a library package that consists of a dashboard template containing saved queries that allows users to specify a base Falcon URL to use for Falcon UI linkage to Threat Actor information. It must be installed on a view that builds on top of FLTR data and firewall data, and firewall data must be normalized first.
To install the dashboard:
Create a view that groups together data from your FLTR repository and your firewall repository. We recommend naming it firewall-fltr-detections.
Inside the new view, click and then on the bottom left. Then search for
crowdstrike/fltr-firewall-adversariesand install the LogScale package.Under go to under Packages and select the crowdstrike/fltr-firewall-adversaries package from the Installed packages list.
Click the
Assetstab and open thez_Falcon_URL_Definitionquery. Here you need to specify your base Falcon URL to use for Falcon UI linkage for Threat Actor information. Uncomment the URL value in that query that applies to your Falcon cloud region.
Package Contents Explained
The dashboard in this package consists of the following widgets:
Threat Actors
Threat Actors - Associated Locations
Threat Actors - Hits by Country
IOS Actor Details
Note that you can click on the Threat Actor name to get more threat intelligence details from the Falcon platform
IoCs without Threat Actors - Associated Locations
IoCs without Attribution
Dashboard Widgets
As part of the schema, there are three widgets included:
A pie chart of detected IoCs by associated Threat Actor groups
A world map of detected IoC Threat Actor locations, and
A time series chart indicating IoC associated country.
Note
This package also contains the following assets that are needed by the dashboard:
z_Falcon_URL_Definition query.
Geo mapping file.
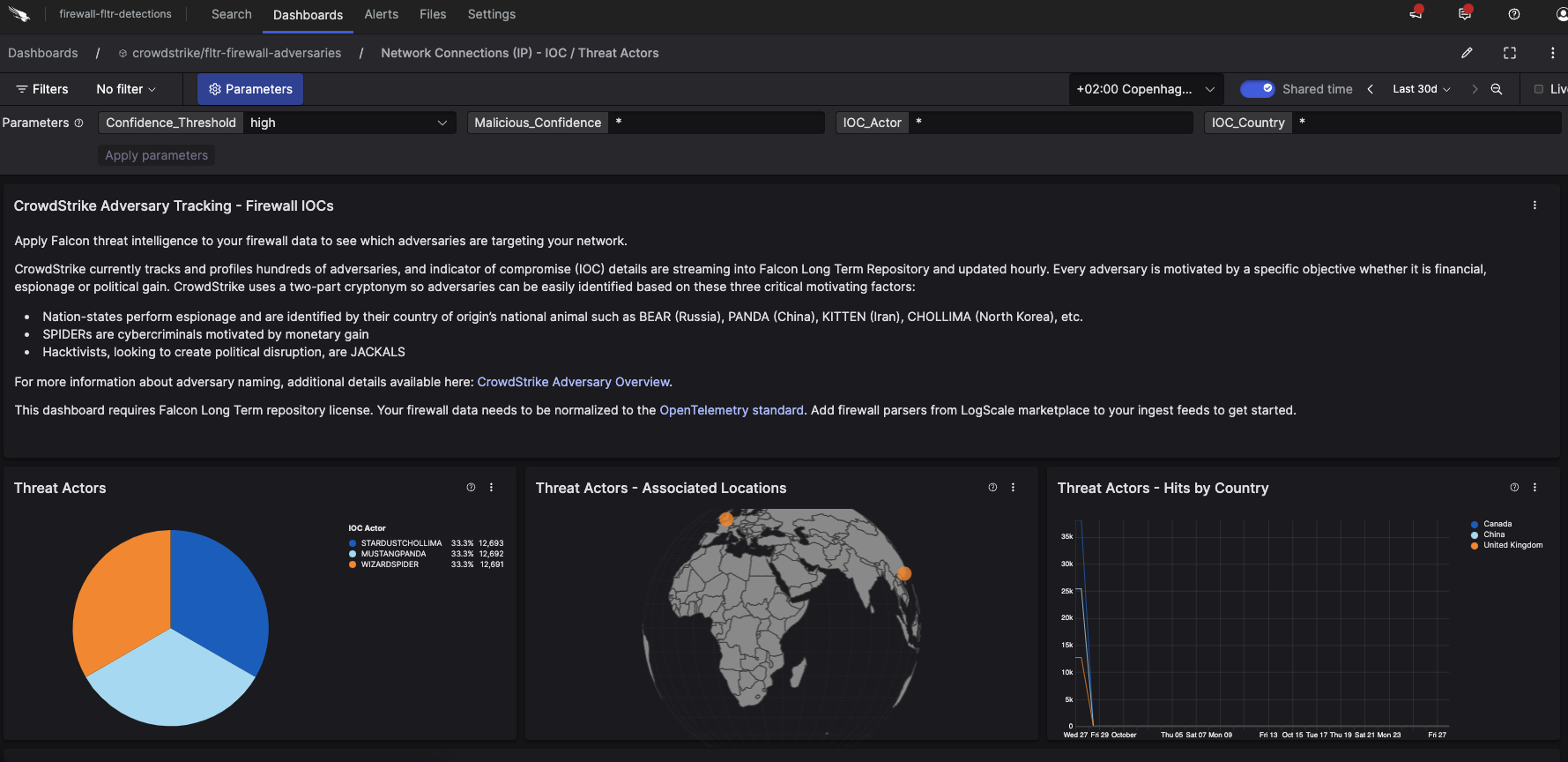 |
Figure 35. Dashboard with example data